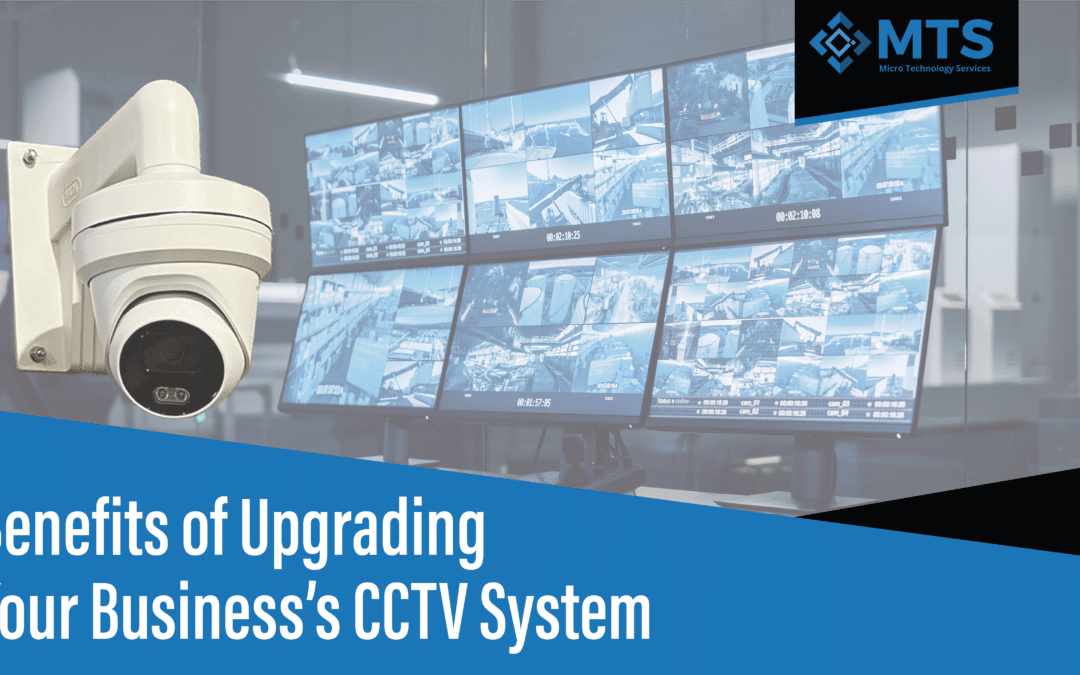
by Liam Etherington | Jul 15, 2024 | Blog
It is more important than ever to secure your business premises in the current fast-paced climate of today. As an IT technician, I have personally experienced how the latest CCTV systems can improve commercial security. AI Detections One of the latest advancements in... 
by Marketing Team | Feb 15, 2023 | Blog
Every business network has one weakness: people. Over the years, cybercriminals have used many social engineering techniques to exploit this weakness. Knowing what the most common types of social engineering attacks are is essential for avoiding them. What Are Social... 
by Marketing Team | Feb 8, 2023 | Blog
When your information system was first built, it was a significant investment to set it up. All that investment and the critical processes that rely on those systems can mean it is difficult to justify the cost. Yet in almost all cases, a new and more automated... 
by Marketing Team | Feb 1, 2023 | Blog
The Cloud is a key step for your business’s digital transformation. It allows for more flexibility in your working environment. Reliability is another key factor in migrating to the cloud. There are many other benefits of the cloud, such as cost-saving, ease of... 
by Marketing Team | Jan 18, 2023 | Blog
Every business owner expects reliable support from their service providers. This is especially important where IT is concerned since nowadays a large number of business operations rely on the cloud. It’s clear that having IT support is a must, but the... 
by Marketing Team | Jan 11, 2023 | Blog
Turning something off sounds simple. Switch off the lights when not in use, or press a button on your remote control to turn off your TV. So, why isn’t it that simple to turn off your computer? Turning off your PC by tapping the power switch off or unplugging...





